Secure Your Crypto in Seconds: The Ultimate Guide to Trezor Wallet Login
In the fast-evolving world of cryptocurrencies, safeguarding your digital assets has never been more crucial. While crypto exchanges offer convenience, they often lack the security of dedicated hardware wallets. Among the top choices for security-conscious users is Trezor, a trusted name in cryptocurrency hardware wallets. Understanding how to navigate the Trezor Wallet login process is essential to ensuring your crypto remains safe, accessible, and under your control.
Why Trezor Wallet Login Matters
Trezor is designed to keep your private keys offline, which drastically reduces the risk of hacks, phishing attacks, and malware. Unlike software wallets or exchange accounts, your keys are stored on a physical device that only you can access. However, the security of your Trezor wallet relies heavily on the login process. A secure login ensures that only authorized users can access funds, manage accounts, or initiate transactions.
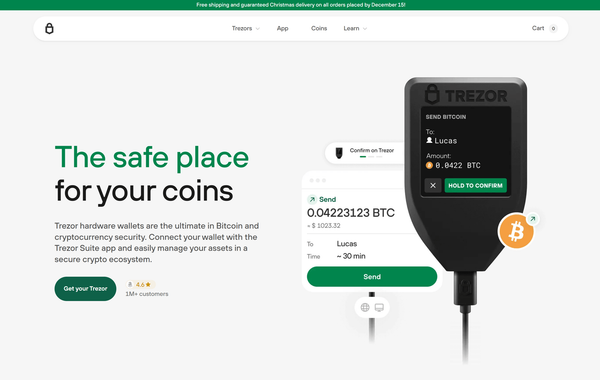
The login process for Trezor is not only about entering credentials; it’s about interacting securely with your hardware device. When you log in to your Trezor Wallet, you are confirming your identity via the Trezor device itself. This multi-layered authentication process is what sets Trezor apart from conventional wallets.
Steps to Log in to Your Trezor Wallet
Logging into your Trezor wallet is straightforward, but it requires careful attention to detail. Here’s a step-by-step guide:
- Connect Your Trezor Device: Start by plugging your Trezor hardware wallet into your computer using the USB cable provided. Trezor devices are compatible with both Windows, macOS, and Linux systems.
- Access Trezor Suite: Navigate to the official Trezor Suite
- application. Trezor Suite is the official desktop and web application that manages all your crypto assets. Ensure you are on the authentic site to avoid phishing scams.
- Enter Your PIN: Your Trezor device will prompt you to enter your PIN. This PIN is unique to your device and protects against unauthorized access. The on-screen interface on your Trezor randomly rearranges the number pad, which prevents keyloggers from capturing your PIN.
- Confirm Your Device: Once the PIN is entered, the device will display a confirmation screen. This ensures that you are interacting with your actual hardware wallet and not a fraudulent application.
- Access Your Wallet Dashboard: Upon successful login, Trezor Suite will display your wallet dashboard. Here, you can view balances, send and receive cryptocurrencies, and manage multiple wallets securely.
Tips for a Secure Trezor Wallet Login
While Trezor is inherently secure, following best practices during login can further protect your assets:
- Always Verify the URL: Whether using Trezor Suite or Trezor Web, always ensure the URL is legitimate. Cybercriminals often mimic login pages to steal your credentials.
- Keep Your Device Firmware Updated: Regularly update your Trezor firmware. Updates often include security patches and new features.
- Avoid Public Networks: Logging into your wallet over unsecured public Wi-Fi increases the risk of attacks. Use a secure and private network.
- Never Share Your Recovery Seed: Your 24-word recovery seed is the ultimate key to your funds. Never enter it online or share it with anyone.
Common Issues During Trezor Login
Despite its simplicity, users occasionally face login issues:
- Device Not Recognized: Ensure your USB cable and port are functional. Sometimes switching ports resolves connection problems.
- Forgotten PIN: If you forget your PIN, your funds are still safe. You can restore your wallet using your recovery seed on a new Trezor device.
- Outdated Trezor Suite: An outdated application may fail to recognize the device. Updating the app often resolves this problem.
Conclusion
Logging in to your Trezor Wallet may seem simple, but it’s the gateway to securely managing your cryptocurrency. By following the official login steps and adhering to security best practices, you can confidently access your digital assets without exposing them to unnecessary risks. Trezor Wallet login is more than just a procedure; it’s a vital part of responsible crypto ownership.
For those ready to experience secure crypto management, visit the official Trezor website to get started: https://trezor.io/start
. Your digital assets deserve the highest level of protection, and Trezor ensures that security begins with a safe and reliable login process.